Security Inspection Checklist free printable template
Show details
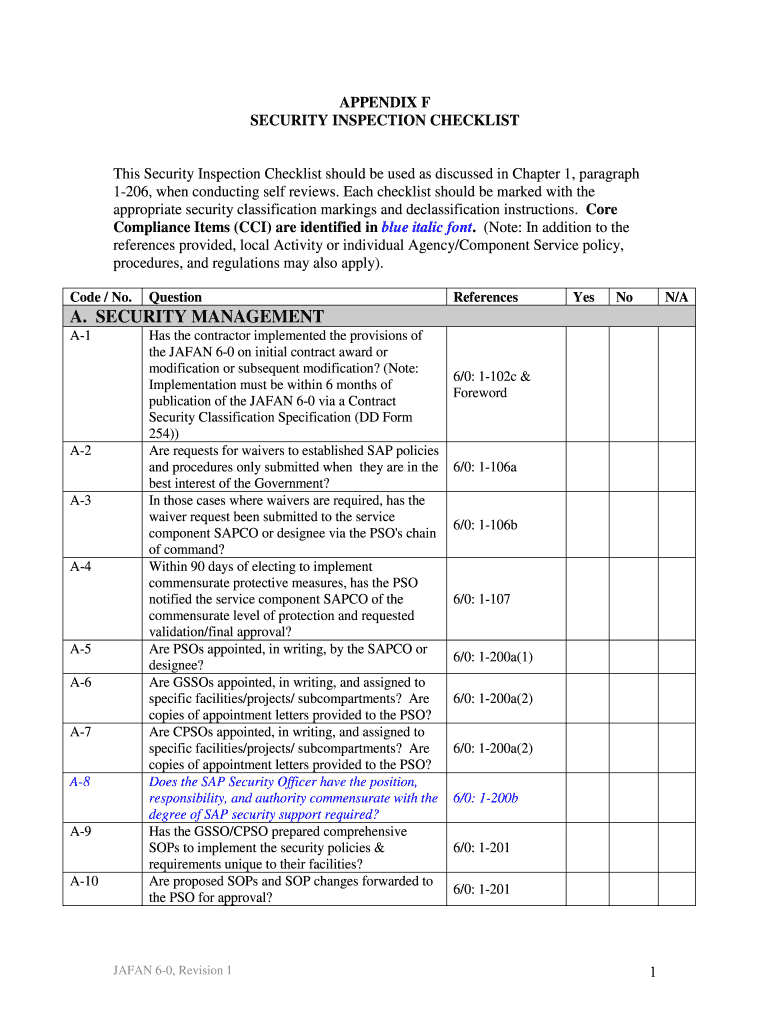
Este documento proporciona una lista de verificación para las inspecciones de seguridad, utilizada durante revisiones internas, abordando diversos aspectos de gestión de seguridad, planificación,
pdfFiller is not affiliated with any government organization
Get, Create, Make and Sign security review checklist form

Edit your security guard daily checklist form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your daily checklist for security guards form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing security guard checklist online
Use the instructions below to start using our professional PDF editor:
1
Set up an account. If you are a new user, click Start Free Trial and establish a profile.
2
Upload a document. Select Add New on your Dashboard and transfer a file into the system in one of the following ways: by uploading it from your device or importing from the cloud, web, or internal mail. Then, click Start editing.
3
Edit daily security guard inspection checklist form. Rearrange and rotate pages, add and edit text, and use additional tools. To save changes and return to your Dashboard, click Done. The Documents tab allows you to merge, divide, lock, or unlock files.
4
Get your file. Select your file from the documents list and pick your export method. You may save it as a PDF, email it, or upload it to the cloud.
It's easier to work with documents with pdfFiller than you can have ever thought. You may try it out for yourself by signing up for an account.
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out security guard checklist template form

How to fill out Security Inspection Checklist
01
Gather all necessary materials, including the checklist template and any relevant security documents.
02
Review the checklist items carefully to understand what is required for each point.
03
Begin with the first section of the checklist, typically focusing on physical security measures.
04
For each item, assess the current security measures in place and mark them as compliant or non-compliant.
05
Provide additional notes or observations where necessary to clarify the assessment.
06
Continue this process through each section of the checklist, paying close attention to detail.
07
After completing the checklist, review all entries for accuracy and completeness.
08
Submit the completed checklist to the appropriate authority or store it securely for record keeping.
Who needs Security Inspection Checklist?
01
Security personnel responsible for maintaining safety and compliance.
02
Facility management teams overseeing security measures.
03
Employees who may need to understand the security protocols of their workplace.
04
Regulatory bodies that require evidence of security inspections.
05
Consultants conducting security assessments for companies.
Fill
security guard checklist pdf
: Try Risk Free






People Also Ask about security inspection
What is a special access program facility?
Definition(s): A specific physical space that has been formally accredited in writing by the cognizant program security officer (PSO) that satisfies the criteria for generating, safeguarding, handling, discussing, and storing classified or unclassified program information, hardware, and materials.
What is the special access program for security clearance?
The Special Access Program (SAP) is a high state of enforced need-to-know and only a minimum number of cleared employees are given access to SAP information. For example, those with SAP access have clearances at the SECRET and TOP SECRET levels.
What is the purpose of a special access program?
Special Access Programs, referred to as SAPs, aim to protect national security by employing enhanced security measures to strictly enforce need-to-know. They also have safeguarding and access requirements that exceed those normally required for information at the same classification level.
Which of the following can approve a request for visit to a SAP facility?
When a visitor is coming to a government or contractor SAPF, the request for the visit must be formally transmitted via a SAP Visit Request or other electronic means approved by the Government Program Manager (GPM) or contractor Program Manager (CPM) as appropriate or their designee.
What is a key difference between special access programs SAPs and other classified programs?
What is a key difference between Special Access Programs (SAPs) and other classified programs? SAPs are a specific class of classified information with additional safeguarding and access requirements above that of other classified information and material.
Which of the following has authority to approve foreign national's entry into a SAP facility?
12. Only the Secretary or Deputy Secretary of Defense may approve access of foreign nationals to DoD SAPs.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I get printable security guard daily checklist?
With pdfFiller, an all-in-one online tool for professional document management, it's easy to fill out documents. Over 25 million fillable forms are available on our website, and you can find the security inspection checklist in a matter of seconds. Open it right away and start making it your own with help from advanced editing tools.
How do I edit security guard vehicle inspection checklist on an iOS device?
Yes, you can. With the pdfFiller mobile app, you can instantly edit, share, and sign security guard inspection checklist on your iOS device. Get it at the Apple Store and install it in seconds. The application is free, but you will have to create an account to purchase a subscription or activate a free trial.
How do I edit vehicle security checklist on an Android device?
Yes, you can. With the pdfFiller mobile app for Android, you can edit, sign, and share vehicle checklist for employees on your mobile device from any location; only an internet connection is needed. Get the app and start to streamline your document workflow from anywhere.
What is Security Inspection Checklist?
A Security Inspection Checklist is a formal tool used to evaluate the security measures and protocols in place at a facility or event. It outlines specific criteria to ensure that all security aspects are reviewed systematically.
Who is required to file Security Inspection Checklist?
Individuals responsible for security management, such as security officers, facility managers, or event organizers, are typically required to file the Security Inspection Checklist.
How to fill out Security Inspection Checklist?
To fill out a Security Inspection Checklist, review each item listed, provide details on compliance or necessary improvements, and include any observations or notes. Ensure that the checklist is signed and dated by the individual conducting the inspection.
What is the purpose of Security Inspection Checklist?
The purpose of the Security Inspection Checklist is to systematically evaluate and ensure that security protocols are adequately implemented, identify potential vulnerabilities, and document compliance with security standards.
What information must be reported on Security Inspection Checklist?
The Security Inspection Checklist must report information such as the date of inspection, inspector's name, security measures in place, identified issues or non-compliance, recommendations for improvement, and any other relevant observations.
Fill out your Security Inspection Checklist online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Security Survey And Inspection Report Sample is not the form you're looking for?Search for another form here.
Keywords relevant to security guard handover checklist
Related to api security checklist pdf
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.
























